In this article, we explain how to successfully run UpSearch’s proprietary Microsoft SQL Server inventory Tool (‘Tool’ or ‘Application). The Data Estate Assessment utilizes this Tool, an on-premises, agentless desktop Application with a small installation footprint. The digitally signed and antivirus whitelisted Tool finds, verifies, and securely collects information about each Microsoft SQL Server instance and the underlying Windows Operating System.
Step 1: Download & Install
Your order confirmation included a download link, which can also be found by logging in to this website. Review Resource Requirements before clicking the link and downloading the installation Setup Wizard. Keep in mind:
- Local Administrator credentials are required on the machines being scanned.
- We recommend running the Application outside of scheduled maintenance windows.
- Run the installation wizard on the machine that will be used to perform the scan.

Once the Tool launches, you will be prompted to read the End-User License Agreement.
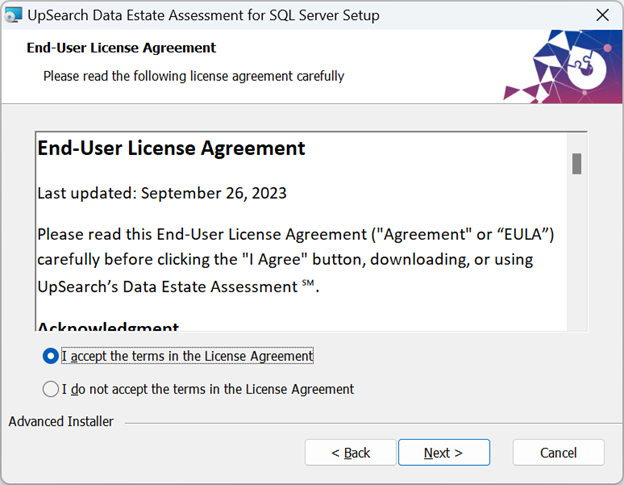
After accepting the License Agreement, select the installation folder.

Click Browse to change the current destination folder.
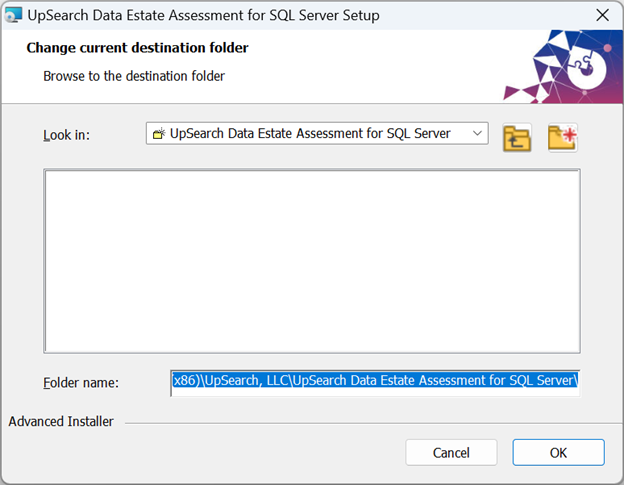
Once the destination folder has been selected, click Install to begin installation.
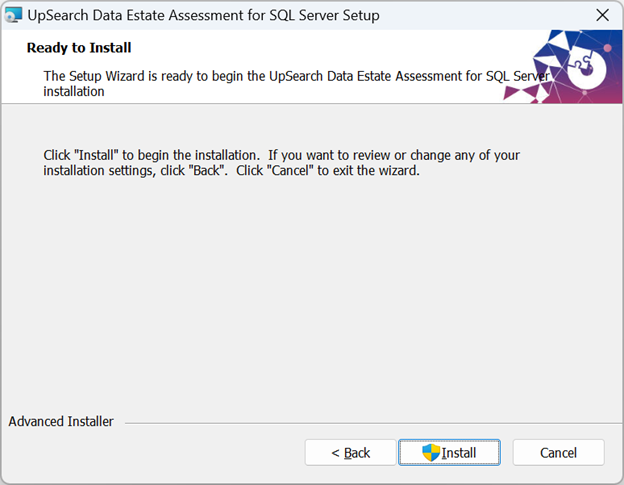
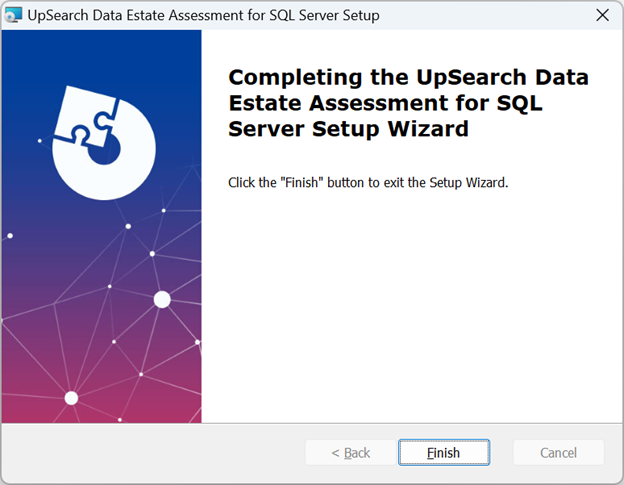
Once the installation process completes, click Finish to exit the Setup Wizard.
After the Setup Wizard closes, you will find this application icon on your desktop.
![]()
Step 2: Run Application
Double click on the desktop icon to launch the application. This splash screen confirms the successful launch of the application.

Configuration Menu
The Tool features a Configuration Menu designed to streamline the management of your Assessment Scope and Output values, saving you time and effort.
Menu Options:
- New: Create a new configuration file.
- Open: Load an existing configuration file to quickly access and apply previously saved values, saving time on reconfiguration.
- Save: Save all current values to the active configuration file.
- Save As: Save all current values to a new configuration file.
- Clear: Remove all currently entered values from the form.
Assessment Scope Tab
The Tool provides multiple Discovery Methods for Domain Administrators to identify and locate SQL Server instances. It will find, verify, and collect information about each Microsoft SQL Server instance and the underlying Windows Operating System using any of the following Discovery Methods, which can be found in the drop-down menu:
Main Discovery Methods
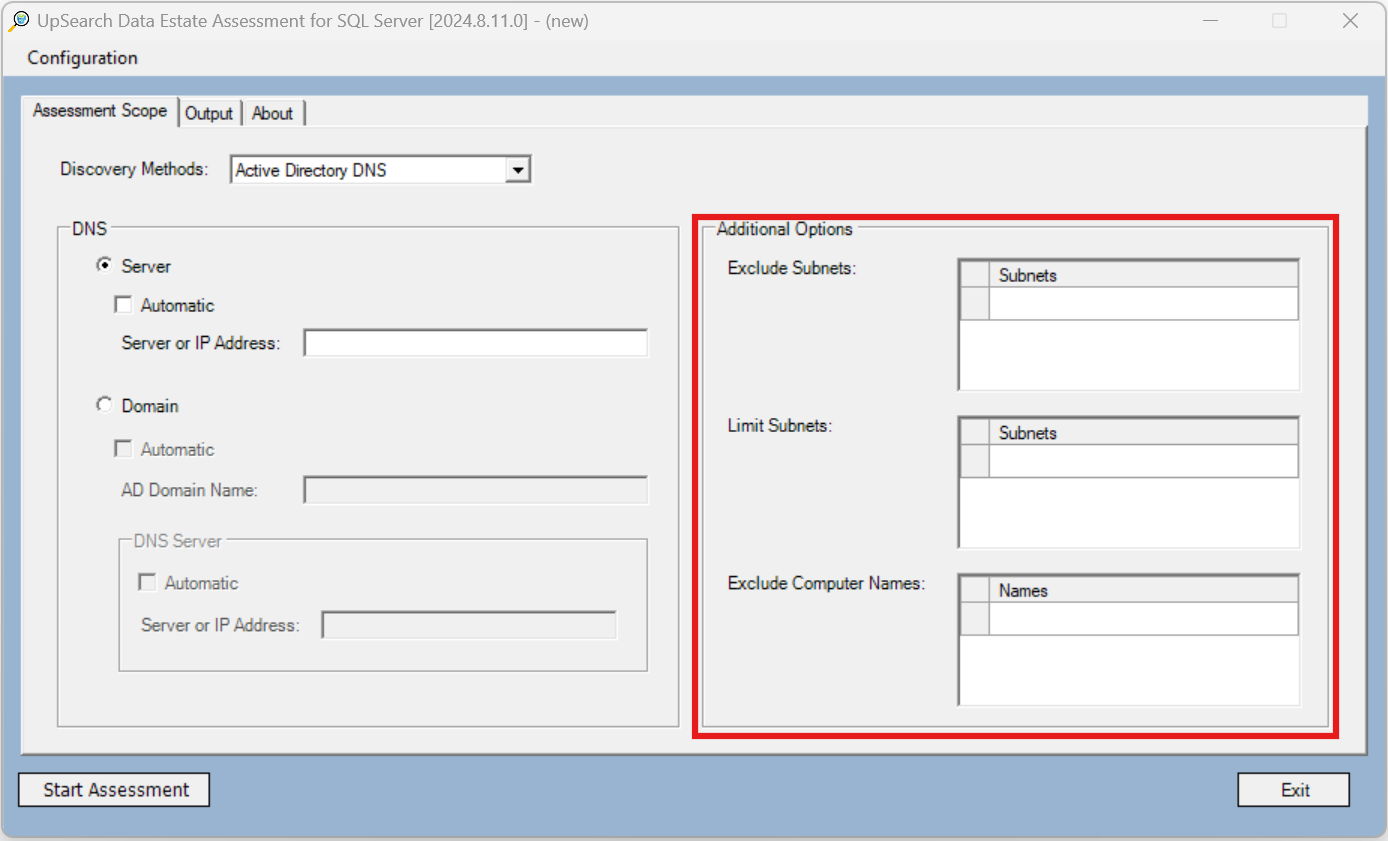
- Active Directory DNS
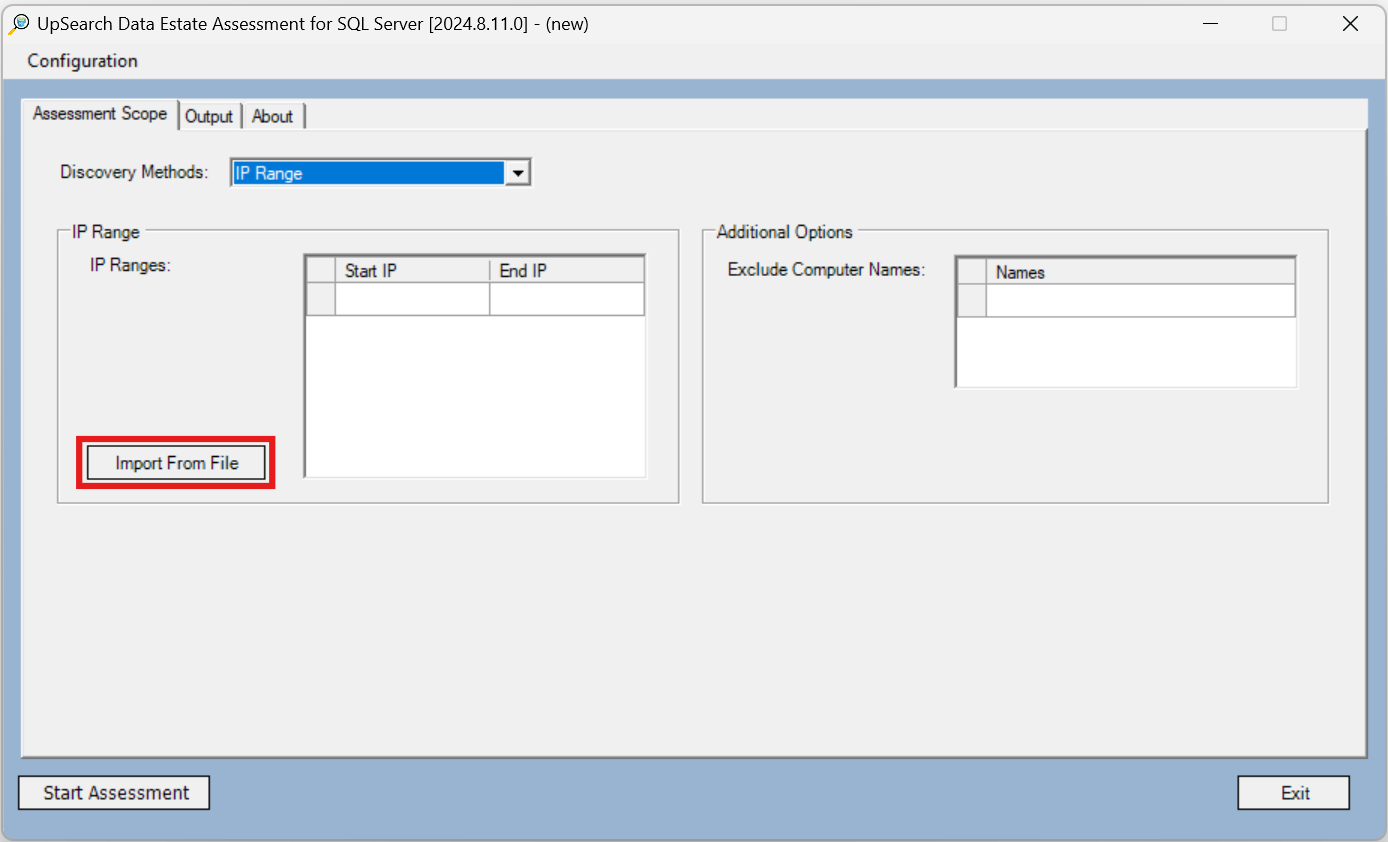
- IP Subnet
- IP Range, required for public domains
Import Files: IP Ranges
After selecting IP Range from the drop-down menu, click Import From File to populate the IP Ranges list from a file containing comma separated values (CSV). The CSV file can contain values in a single line or multiple lines. Use a colon (:) to separate the IPs in each range. CSV file content format examples:
10.0.0.0:10.0.0.255,11.0.0.0:11.0.0.255,12.0.0.0:12.0.0.255
or
10.0.0.0:10.0.0.255,
11.0.0.0:11.0.0.255,
12.0.0.0:12.0.0.255
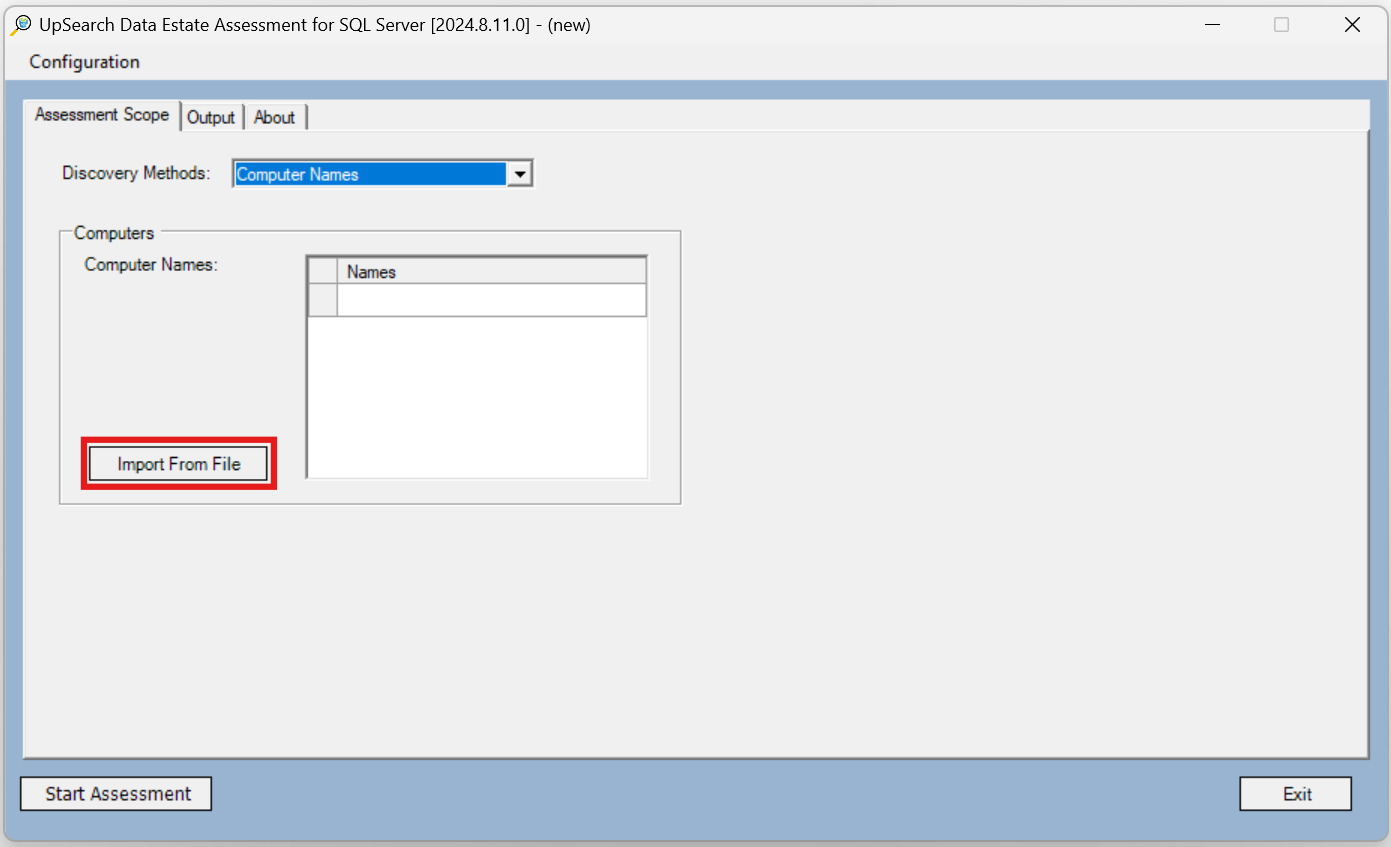
- Computer Names
Import Files: Computer Names
After selecting Computer Names from the drop-down menu, click Import From File to populate the Computer Names list from a file containing comma separated values (CSV). The CSV file can contain values in a single line or multiple lines. CSV file content format examples:
ComputerA,ComputerB,ComputerC
or
ComputerA,
ComputerB,
ComputerC
Additional Discovery Options
- Exclude Subnets
- Limit Subnets
- Exclude Computer Names
Browse related knowledge base article: SQL Server Discovery Methods.
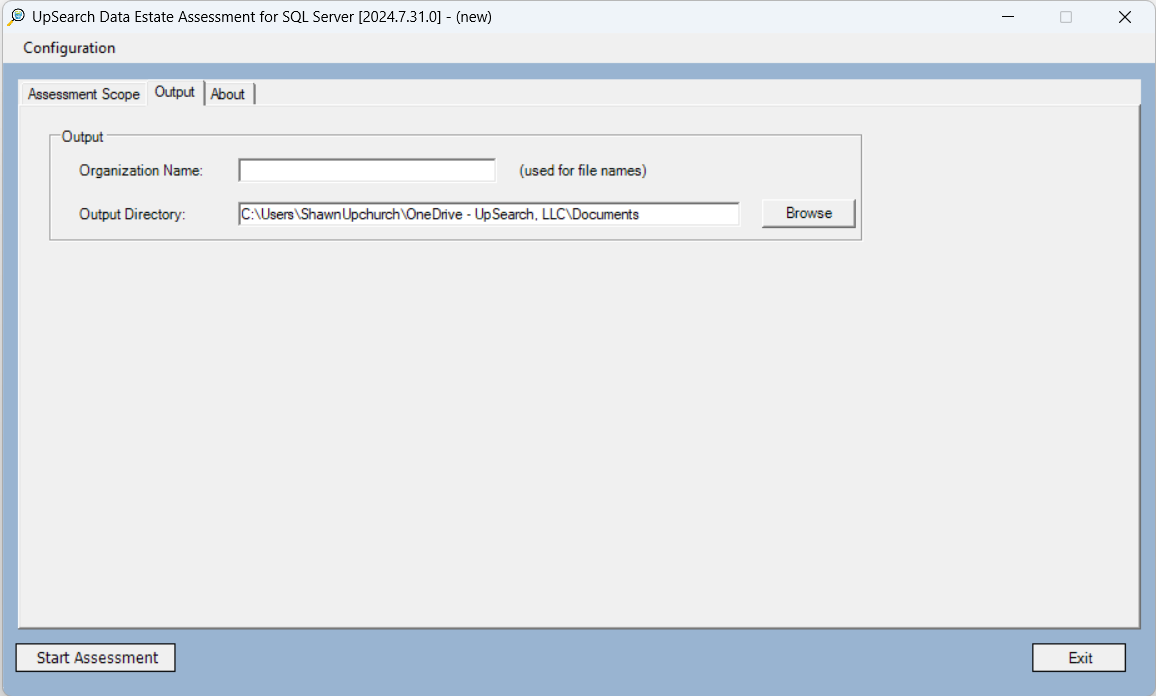
Output Tab
The following output settings are used for the name convention and placement of the output files.
- Organization Name: Specify the common use name of your organization for file naming purposes. For example, if your organization name is “UpSearch”, the Tool will name the output file as “UpSearch-2024-02-05-19-39.zip”. Capitalization is retained and the output files are date and time stamped.
- Output Directory (optional): Specify the literal path to the directory where you want the output files to be saved. If you do not provide a path, the system will use the ‘My Documents’ folder. Please make sure the directory allows write access.
Browse related knowledge base article: Output Settings.
When you’re ready, click Start Assessment and the scan will begin immediately. The scan operates very lightly and doesn’t require scheduling outside of business hours, although we recommend running the Application outside of scheduled maintenance windows.
Collection Results
To ensure the confidentiality and security of your data, assessment results and log file are SHA-256 encrypted and stored in a zip file. Furthermore, it is important to note that UpSearch retains exclusive control over the SHA-256 encryption key for the encrypted file. This stringent security measure ensures the safe and confidential transfer of your results, facilitating seamless processing and comprehensive analysis.
Step 3: Upload Results
Log into your account to securely upload your results (zip file) to UpSearch’s protected environment. Once your results are received, we will analyze them and inform you if any additional information is needed. We will then create your Data Estate Assessment report and inventory.
For any questions about these instructions, please contact us via the following page on our website: UpSearch Contact Us.